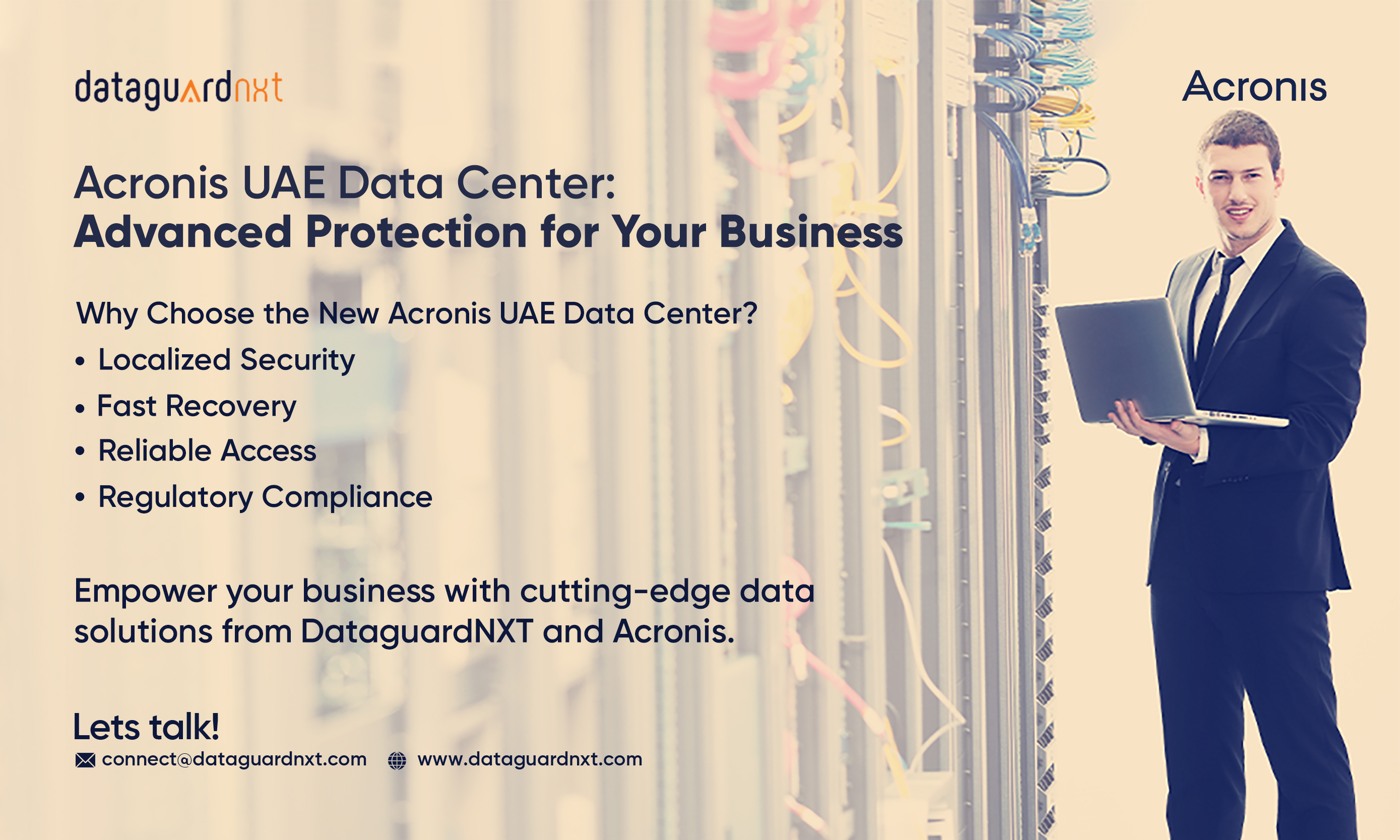
How a SOC Can Help Keep Your Enterprise Safe from Cyber Risks?
Liby Sep 5, 2023

The Importance of Endpoint Security in Today's Threat Landscape
Karen Aug 22, 2023

What makes Indefend superior to Forcepoint?
Akhdar Aug 2, 2023

Bitdefender Gravityzone vs ESET Protect Advanced Cloud
Akhdar Jul 12, 2023

Cybersecurity and Artificial Intelligence: AI's Potential Dangers
Liby Jul 26, 2023

Will AI Replace Cybersecurity Jobs?
Kerman Jul 12, 2023

What are the key functions of data management?
Carlos Gotay Jul 7, 2023

Mastering Data Management: Best Practice for Effective Data Management
Naseer Jul 4, 2023

Why is multi-layered security important?
Skey Jun 22, 2023

How XDR Can Revolutionise MSP Cybersecurity?
Naseer Jun 20, 2023

DLP MSP Framework
Kathy Jun 13, 2023

What are cybersecurity assessment?
Karen Jun 9, 2023

What is the VAPT process.? #Cybersecurityassured #dowithdataguard
Eroglu Jun 8, 2023

Is vCISO services a new revenue stream for MSPs? #Cybersecurityassured #dowithdataguard
Andresson Jun 7, 2023

Guarding Against the Unseen Threat: Cyber Security and its impact on the Professional Landscape
Werner Jun 6, 2023

RealCISO vs Cynomi: The Battle for the Best vCISO Platform
Naseer Jun 2, 2023

How is vCISO vital for your business?
Kerman May 30, 2023

Top IT Security Best Practises: Workstation Security
Naseer May 30, 2023

vCISO, the ideal Platform for Service Providers
Naseer May 23, 2023

Cybersecurity in schools: a sanctuary for cybercriminals?
Jure May 18, 2023

Five strategies to make your MSSP stand out
Peter May 17, 2023

Bitdefender: How to win against Microsoft Defender
Rybicki May 15, 2023

Bitdefender outperforms Sophos in threat detection
Karen May 11, 2023

Automation of advanced monitoring with Acronis Cyber Cloud
Karen May 5, 2023

Bitdefender XDR and MDR for MSPs
Rybicki Apr 28, 2023

Acronis Cyber Cloud DR for Industry Compliance
Tooele County Apr 26, 2023

MSP Cybersecurity Checklist for Ransomware and Other Threats





































































.jpg)