


Key user activity tracking insights are at your fingertips with an intuitive, configurable dashboard.


The AI-powered technology at Veriato examines user behavior trends and notifies you automatically of any unusual or questionable activities.


Real-time alerts regarding unauthorized and suspected activity let you take prompt action to safeguard your vital information.


Strong, user-friendly solutions that maintain the engagement and productivity of your office, hybrid, and remote teams.

Veriato workforce behavior analytics go beyond passive monitoring to proactively analyze productivity, monitor for insider risk and much more.
Powerful, easy-to-use tools to keep your remote, hybrid and office teams productive.
Veriato’s AI-powered algorithm analyzes user behavior patterns and automatically alerts you to any abnormal or suspicious activity.
Assign productivity scores to websites, programs, and applications.
Select between three types of screenshots: Continuous, Keyword Triggered and Activity Triggered.
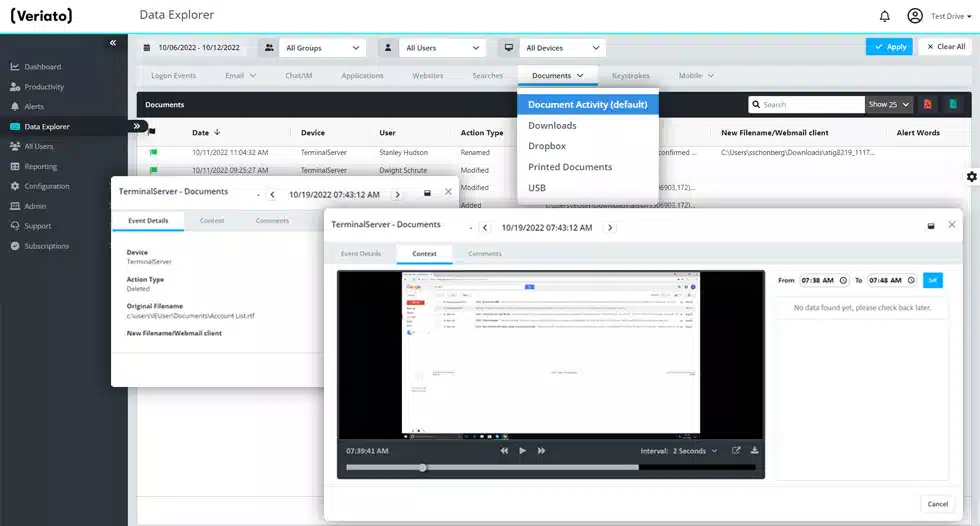
Track activities on local, removable, and cloud storage, as well as print operations. See when files are created, edited, deleted, or renamed.
Set flexible work hours by team/department and decide when tracking starts and ends throughout the day.
Choose from many preset reports or customize your own. Set up real-time alerts that fit your productivity metrics.
Veriato protects your organization from insider threats with predictive behavior analytics and user activity monitoring.
Captures all application usage to provide true reporting on what applications are being used, by who, and for how long.
Identify opinions expressed in email text to determine the writer’s sentiment.
Choose between three types of screenshots: Continuous, Keyword Triggered and Activity Triggered.
Capture and analyze communication activity in traditional email clients as well as many popular webmail services.
Autonomously capture connections made by applications, including ports used and bandwidth consumed.
Track activities on local, removable, and cloud storage, as well as print operations. See when files are created, edited, deleted, or renamed.
Veriato helps your organization detect financial fraud, data theft and other employee misconduct.
Capture and report on communications activity occurring on commonly used messaging apps. Record web activity, including webmail usage, file uploads.
Capture and analyze communication activity in traditional email clients as well as many popular webmail services.
Choose between three types of screenshots: Continuous, Keyword Triggered and Activity Triggered.
Collect all application usage to provide true reporting on what applications are being used, by who, and for how long.
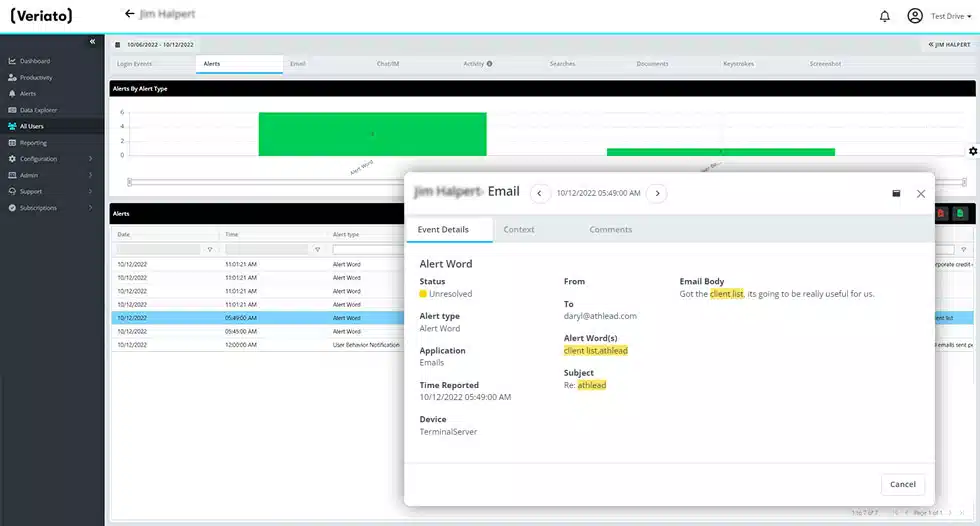
Record every keystroke, including “hidden” characters and combinations and trigger real-time alerts based on specific keywords.
Track activities on local, removable, and cloud storage, as well as print operations. See when files are created, edited, deleted, or renamed.
Veriato reduces administrative burden of corporate or regulatory compliance and improves your audit readiness.
Ensure compliance by monitoring activity across applications, email, chats, files, internal network, web and much more.
Identify opinions expressed in email text to determine the writer’s sentiment.
Get reporting and real-time alerts whenever potential fraudulent or illegal activity is detected.
Choose between three types of screenshots: Continuous, Keyword Triggered and Activity Triggered.
Autonomously capture connections made by applications, including ports used and bandwidth consumed.
Track activities on local, removable, and cloud storage, as well as print operations. See when files are created, edited, deleted, or renamed.
Rest easy – your data is in safe hands!
The actions, attendance, and productivity of employees are tracked using employee monitoring software. This covers all digital activity done on devices registered with or owned by the company.
There is software available for Android devices, Macs, PCs, and Chromebooks for remote monitoring. It can operate covertly in the background once installed.
This program will monitor and log every action the user takes in great detail. The user's past web searches, idle time, instant chats, file movements, productivity, downloads, uploads, print jobs, USB device usage, network access, and more are all accessible.
The software keeps track of how long a program is used automatically each time it is opened. A productivity tracking report is created using this data to show you where your staff members are spending the majority of their time.
Because remote monitoring software records the user's screen, it also functions as a digital surveillance camera. This enables you to determine their actions and comprehend their productivity and labor-intensive duties.
Veriato, an insider threat management system, may assist you in tracking user activity, keeping an eye on your most critical data, and anticipating security breaches before they happen. It will also assist you in conducting audits, making sure regulations are followed, and reacting fast to any data breaches.
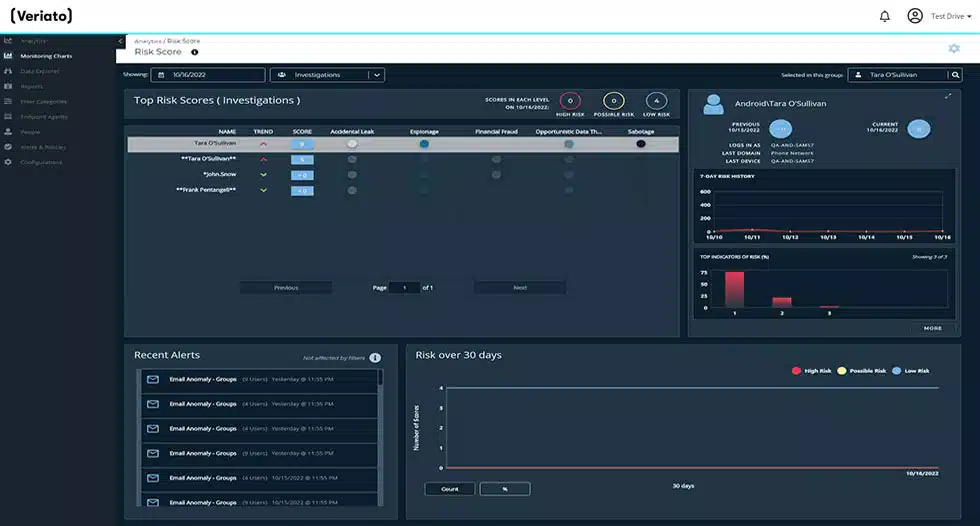
Veriato uses machine learning to evaluate user activity, identify risk variables, and generate risk scores for each monitored user. This allows you to go beyond insider risk detection and proactively monitor for threats
The following five actions are recommended to lower the possibility of insider attacks in your company: